Release Notes
Version 5.6
Fudo Enterprise 5.6.4
Date: January 2026
This is a minor Fudo release, introducing a range of improvements and new fixes.
NEW FEATURES AND IMPROVEMENTS
- Improved Discovery configuration by allowing empty server pools to be selected as targets for newly discovered domain accounts, enabling their use as placeholders even when no servers are assigned yet.
- Restored the previous behavior of grouping nested SSH sessions under the main session in the sessions list and system reports, replacing the separate-session view.
- Improved Web Client keyboard handling for single open connections, ensuring the TAB key is consistently passed to the target session and not intercepted by the browser, preventing focus loss or unintended autocomplete behavior.
- Improved web application security with Content Security Policy headers to protect against cross-site scripting attacks.
- (Beta) Introduced Rendered HTTP functionality in ShareAccess. Note: Using this feature requires accepting a self-signed certificate.
DISCONTINUED FEATURES
- Removed support for PyMySQL libraries for Python.
- Fudo Enterprise 5.6 no longer supports the DHCP.
- Fudo Enterprise 5.6 no longer supports the APIv1. All scripts using APIv1 should be rewritten to use APIv2.
- Grant-related endpoints have been removed in this release. Please update your integrations accordingly. For more information, refer to the updated API documentation.
- Disabled access to the /api/v2/diagnostics endpoint.
- Fudo Enterprise 5.6 no longer supports the Application to Application Password Manager.
- Fudo Enterprise 5.5 and 5.6 no longer supports the Mobile Token authentication method used to bind the Fudo Officer mobile application to a User. You must unlink all Fudo Officer bindings from Users configuration before the upgrade. For more details, please refer to the 'Before You Upgrade' section below.
ANNOUNCEMENTS
- Certificate chain verification – Fudo now verifies the entire certificate chain during server connections. See details later in this document.
- Fudo Enterprise 5.6 is the last version supporting transparent and gateway modes in the listeners configuration. Listeners using these modes must be reconfigured to use proxy and bastion modes before upgrading to the next release.
- Fudo Enterprise 5.6 is the last version to support bridge interfaces and network interface cards with bypass mode. These components are tightly coupled with the transparent and gateway modes, which will also be removed in version 5.7. We recommend reviewing your network configuration to ensure compatibility with future versions.
- Support for the Telnet 3270 protocol is under review and may be removed in a release following version 5.6. If this protocol is critical to your environment, please contact Fudo Support for more information.
- Support for the 4-Eyes principle, implemented through the Require approval option in safe configuration and used to restrict user access by requiring confirmation, is currently under review and is planned for removal in a future release. Its functionality is largely covered by the Just In Time feature, which we recommend adopting instead. If this functionality is critical to your environment, please contact Fudo Support for more information.
BUG FIXES
- Fixed an issue with certificate chain validation where TLS verification could fail when the configured Root CA was not the direct issuer of the server certificate (longer trust chains). This affected scenarios such as External Authentication or RDP server connections with TLS enabled, where using a Root CA certificate could prevent successful authentication or session establishment.
- Fixed an issue where, during the first-login password change flow for an AD-synced user, removing the AD login from the external authentication method mid-process could cause a crash in the authentication flow and prevent the password from being updated in Active Directory.
- Fixed an issue where, when more than 100 Listeners existed, only the first 100 listeners were displayed when linking an account to a listener in a safe, making listeners beyond this limit invisible.
- Fixed an encoding issue in filter handling where entering special characters such as % or parentheses () in the Search field could trigger a 400 error and leave the UI in a loading state, regardless of whether matching objects existed.
- Fixed an issue where RDP sessions initiated via the xfreerdp client failed to start for RemoteApp connections or were immediately terminated for standard RDP sessions.
- Fixed an issue where opening the session player without sufficient privileges resulted in an indefinite loading spinner with no feedback.
- Fixed an issue where a deleted IP label was still visible and selectable in IP address dropdowns across the management interface.
- Fixed an issue where the system startup could be significantly delayed by becoming stuck in the Starting data state during reboot. Startup handling has been improved to reduce excessive delays and ensure a reliable transition to the RUNNING state.
- Fixed an issue where Sound Redirection, configured in Safe settings, worked only when Dynamic Virtual Channels (DVC) were enabled.
- Fixed an issue where RDP sessions could be randomly terminated after ending a SIP connection when Dynamic Virtual Channels (DVC) were enabled.
- Fixed an issue where files larger than 50 MB downloaded from Downloads → Files lost their original filename and extension after being transferred via SCP.
- Fixed an incorrect label in Sensitive logs retention settings.
- Fixed an issue where credential injection could fail on certain websites due to an unhandled error message, causing the browser script to stop instead of proceeding to load the page.
- Fixed a missing translation in the Scheduled Access Request popup for Just-in-Time access, which previously prevented the request from being displayed correctly.
- Fixed an issue where the vote counter for access requests displayed an incorrect number of votes when approvers lacked capabilities to the voter objects.
- Fixed incorrect handling of popup windows and external application prompts in rendered HTTP sessions by redirecting them to the main session window, restoring proper behavior of standard refresh and navigation shortcuts.
- Restored the Select all option in the Sessions tab, which was no longer available starting from version 5.6.1.
- Remove deprecated /api/v1/ endpoints related to Discovery functionality that have been replaced by /api/v2/ equivalents, and update the frontend to use the existing /api/v2/ endpoints instead.
- Fixed an issue in the Servers list where the All sub-tab did not display all available servers for the selected protocol.
- Fixed an issue where IPv6 addresses configured in Network configuration were not available for selection in the Local address dropdown when creating listeners or servers.
- Fixed an issue where a failed upgrade from version 5.6.x due to configuration problems could freeze the upgrade process, preventing further upgrade checks or re-uploading the .upg file.
- Fixed an issue where popup windows and external application prompts during HTTP sessions were not handled correctly and remained open instead of integrating with the main session window. All popups are now redirected to the main window, ensuring consistent behavior. Users can reload redirected pages using the standard browser refresh shortcut, and keyboard navigation shortcuts for going back or forward now work as expected.
- Improved upgrade reliability by automatically fixing invalid LDAP Synchronization configurations during upgrade, removing redundant External Authentication assignments that could cause errors and block subsequent upgrades.
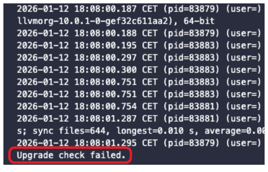
- Fixed an issue where the upgrade check did not clearly report failures when upgrade conditions were not met. The check now displays an explicit error message, allowing administrators to clearly identify incompatible upgrade scenarios.
- Share Access: Verified and stabilized ShareAccess synchronization by correcting expiration date handling; synchronization now completes successfully without parsing errors.
KNOWN ISSUES
- In versions 5.6.0, 5.6.1, and 5.6.3, the upgrade check does not clearly indicate a failure. This is particularly relevant when attempting to upgrade using an image with an older kernel version, where the check appears inconclusive instead of explicitly reporting that the upgrade is not supported.
- Deleting an LDAP/AD mapping that has no Fudo group assigned may incorrectly remove all LDAP-synchronized users from the system. As a result, users are re-created as new objects during the next synchronization, and users from the deleted mapping may still be synchronized once despite the mapping no longer existing.
- After upgrading from 5.5.x to 5.6.3, adding a public TLS certificate to an RDP listener may fail with the error tls_certificate is not a valid X509 certificate chain, due to improvements in certificate chain validation.
- Users assigned to a Safe through group membership may not receive email notifications for ńaccepted or rejected Just-in-Time access requests, even if they have the required role and capabilities.
BEFORE YOU UPGRADE
It is highly recommended to perform the 'Upgrade check' before the proper upgrade. The result of the failed check may contain information about configuration changes that needs to be done by a Fudo administrator to successfully upgrade Fudo.
There are a few things that need to be verified before this upgrade can be applied:
- Make sure your Fudo instance isn’t undergoing any system-wide process, such as storage rebuild, or the system isn’t under full-load.
- In a cluster configuration, make sure all nodes are synchronized and upgrade the slave node first.
- Make sure you have an active Premium or Standard Support maintenance contract.
Upgrade Check Failure Reporting
In versions 5.6.0, 5.6.1, and 5.6.3, the upgrade check does not clearly indicate a failure. In such cases, the check may appear inconclusive instead of explicitly reporting a failure, regardless of the underlying reason (for example, an unsupported kernel version).
Please carefully review the upgrade check outcome to ensure that the upgrade image is compatible with the current system configuration. This is particularly important when attempting to upgrade using an image with an older kernel version, where the check may appear inconclusive instead of explicitly reporting a failure.
TDS Kerberos Delegation
For Kerberos authentication to work correctly, the server configuration must use the Host option in the Destination section. Configurations using an IP address will fail because Kerberos relies on hostname-based SPN (Service Principal Name) resolution.
Licensing Changes
Starting with version 5.6, license enforcement logic has been updated as part of the RBAC introduction:
- In version 5.5, superadmin users were always counted as active and had priority in login rights.
- In version 5.6, logins of users with administrative privileges to the Admin Panel are always prioritized, regardless of the current license limits. Their logins are now counted as standard authentications within the licensing scope.
|
Note: When the number of active users reaches the license limit and a new user logs into the Admin Panel, the system now prioritizes users with management access. In this case, the user who logged into User Access Gateway (UAG) earliest will lose access, as the privileged user is now counted as active. Existing sessions of the user who lost access are not terminated — they continue to run as usual. |
DHCP Discontinuity
Starting from version 5.6.1, DHCP is no longer supported. If DHCP is enabled in the existing configuration, the upgrade process will be blocked. To proceed with the upgrade, ensure that all DHCP-related settings are removed or replaced with static network configuration before initiating the upgrade.
External Authentication - Active Directory
In previous releases, when configuring external authentication through Active Directory with TLS enabled, it was possible to upload a server certificate. Starting from this release, Fudo only supports a CA certificate. If a server certificate is currently configured, you must change its value to None before upgrading.
Handling Legacy Checkout Sessions
During the upgrade to version 5.6.1, environments containing checkout sessions that still reference the deprecated SAFE_SYSTEM_ID are automatically handled as follows:
- Deleted checkout sessions referencing SAFE_SYSTEM_ID are removed.
- A new safe is created with the ID MIGRATED_CHECKOUT_SAFE_ID (value: 200) and the name 'Migrated checkout sessions'.
- Remaining (non-deleted) checkout sessions are reassigned from SAFE_SYSTEM_ID to MIGRATED_CHECKOUT_SAFE_ID.
These changes ensure that the upgrade process completes successfully in environments previously migrated to Fudo 4.3.
|
Note: The safe 'Migrated checkout sessions' is created only if the sessions described above exist in the system. |
Mobile Token
|
Note: Fudo Enterprise 5.6 and later versions no longer support the Mobile token authentication method used to bind Fudo Officer mobile application to a User. Please ensure that the mobile application is unlinked from any User configuration. Otherwise, the upgrade will fail, and the script UPG000685 will return a list of users who have the mobile application linked. |
To unlink the Fudo Officer mobile application, please edit the user configuration, then:
- Go to the 'More' tab, and in the 'Fudo Officer' section, unlink the application using the 'Cancel binding' button.
- Alternatively, go to the 'Settings' tab, in the 'Authentication' section find the 'Mobile token' method and remove it using the 'Delete' button.
Transition to RBAC After Upgrade
|
Note: In the RBAC model, the *-read privilege grants visibility into a specific tab of the interface, and consequently, into all objects of that type in the system—not just those for which the user has capabilities. This privilege provides view-only access and does not permit editing, deletion, or any other actions. |
- Listener Access Model Updated: With the introduction of RBAC, users now either have access to all listeners or to none. Granting access to individual listeners is no longer possible.
- Access Request Voting: Now requires both `access-request-read` and `access-request-vote` privileges, as well as `read` access to the associated user, safe, and account.
- Superadmin, Admin, and Operator Roles After Upgrade: These roles are preserved during the transition to RBAC, with their permissions mapped to ensure comparable access as before. Note that some exceptions apply, and the mapping may not reflect a one-to-one correspondence in all cases. Selected examples include:
- After the upgrade, an admin who has a capability assigned to an object will automatically gain full permissions for that object.
- Since listeners are considered a global and network-level configuration, after upgrading to version 5.6, admin users no longer have permissions to create them.
- The Authentication tab is now available to users with the admin, safe admin and operator roles by default (`extauth-read` privilege) to be able to see or assign external authentication to other users.
- The admin, safe admin and operator roles now have access to the External Password Repositories tab (`passvn-read` privilege) to be able to see or assign external password repositories to accounts.
- The admin, safe admin and operator roles now have access to the Cluster tab (`cluster-read` privilege) by default, allowing them to send sessions to other nodes.
- The operator role now includes the `listener-read` privilege by default. However, due to RBAC changes, operators can currently view all listeners, not just those explicitly granted.
- A user with the session viewer role can now access the Download > Files tab and download files listed there. This permission is required for the correct display of SFTP/SCP sessions.
- The session viewer role now includes access to additional interface elements, such as new tabs (e.g., Users, Servers, Accounts, Safes) and the ability to add the Active Users dashlet from the Dashlet Marketplace, depending on the assigned capabilities.
- Operators, session viewers, safe admin, and other custom roles will now be able to see all existing anonymous sessions as well as any new sessions initiated by anonymous users.
- The predefined user and service roles have been removed.
- After upgrading to version 5.6, any users who previously had this role assigned will no longer have any role.
- Before the upgrade, customers who previously had multiple users assigned to the service role must remove all but one of them.
- SNMP settings previously configured for that user will be transferred to the System tab and applied globally.
|
Note: The predefined roles serve as a transitional starting point and are fully editable (with the exception of superadmin). The automatic mapping of legacy roles is a one-time compatibility step performed only during the upgrade from a version without RBAC. These predefined roles are not intended to replicate previous permissions one-to-one, but rather to provide a starting point for adaptation. We recommend reviewing all assigned privileges after the upgrade to ensure they reflect your security requirements. |
MySQL Listeners
TLS is now required for MySQL listeners. In previous versions, TLS could not be enabled for MySQL listeners or servers. As a result, any existing MySQL listeners will become non-functional after the upgrade. To restore connectivity, administrators must manually enable TLS and configure a valid certificate for the listener.
CA Certificate Verification for MySQL and HTTP Servers
In versions 5.6.0, 5.6.1, and 5.6.3, server certificate verification was not properly enforced when establishing TLS connections to MySQL or HTTP servers using CA-based authentication. The configured CA certificates (Root CA or Sub CA) were not correctly used to verify the server certificate during connection establishment, allowing connections to succeed even when the server presented a certificate not signed by the configured CA.
Kerberos Support for User Directory Synchronization
If you plan to use Kerberos authentication for User Directory synchronization, ensure the following before upgrading:
- Port 88 (Kerberos) is open on the firewall — otherwise, synchronization will fail.
- The Fudo hostname includes the appropriate domain suffix (for example, fudo.qa.kerberos).
- The DNS server from the same domain is properly configured.
- The controller address matches the SPN (Service Principal Name) of the LDAP server defined in the domain.
If your current configuration uses an IP address instead of a hostname, update it to use the correct hostname before upgrading.
|
Note: If you do not intend to use Kerberos, disable it in the Settings > Authentication > Global tab to continue using simple bind for synchronization. |
RECOMMENDED UPGRADE PATH
Before proceeding with the upgrade, please verify the version number of your Fudo Enterprise instance. Depending on the version number, you will need to follow a specific upgrade path. To learn more, please refer to the Fudo Enterprise Product Upgrade Path article.
|
Note: Fudo Enterprise 5.4.12 introduces a new upgrade barrier in the Product Upgrade Path. If you are upgrading from any version of Fudo 5.4, please ensure you upgrade to at least version 5.4.12 before proceeding to version 5.6.x. |
HOW TO UPGRADE YOUR FUDO
|
Note: If your Fudo is running in a cluster, start the upgrade on the Slave node, and only when the upgrade finishes successfully start upgrading the Master node. When both systems are running the same Fudo version cluster communication will be restored. |
- Login to your Fudo Admin Panel.
- Select 'Settings > System' from the main menu on the left-hand side and go to the 'Upgrade' tab.
- Select Upload from the top right side and upload the previously downloaded and unzipped upgrade package file.
- Select Run Check to determine if your upgrade file is correct and can be applied to the existing Fudo configuration. Refresh your browser window to see Upgrade check current progress.
- Review the Upgrade Check results to confirm that the upgrade file can be applied the existing Fudo configuration.
- Upon a successful Run Check result, upgrade your Fudo by using the Upgrade button. Upon system restart, all active sessions will be terminated.
|
Note: In case of an unsuccessful check do not upgrade your system, double check your upgrade file checksum. If you encounter any problems, get in touch with us and we will assist you. |
HOW TO IMPORT SYSTEM CONFIGURATION
|
Note:
|
- Login to your Fudo Admin Panel.
- Select Settings > System from the main menu on the left-hand side.
- Go to the Configuration tab.
- Upload the 'Master key' file and 'Configuration file' exported from another Fudo instance and click Import to proceed with initiating the system with the imported data.
|
Note: For more details, please refer to the 'Exporting/Importing System Configuration' section of the Fudo Enterprise documentation. |
THE ROLLBACK PROCEDURE
If you are experiencing issues with the newly installed version, you have an option to roll back to the previous version of Fudo running on this machine. To do so, click the user menu on the top right, select 'Reboot', and select previous system revision from the drop-down list.
|
Note: Please note that if upgrading from version 5.5 or earlier, both session recordings and any changes to RBAC roles or groups made in the newer version will be lost after rollback. |
DOWNLOAD
Download Fudo Enterprise 5.6.4
Download PDF version of this Release Note.
CONTACT US
If you have questions or concerns, please get in touch at support@fudosecurity.com or by phone: +48 22 100 67 09.
Sincerely,
Fudo Security Team
Fudo Enterprise 5.6.3
Date: November 2025
This is a minor Fudo release, introducing a range of improvements and new fixes.
NEW FEATURES
- Extended AI-powered session summaries to support RDP sessions, in addition to SSH. This enhancement enables administrators to quickly review both SSH and RDP activities using AI-generated summaries, further improving audit efficiency and reducing manual review time.
- Introduced Kerberos support for User Directory synchronization. When Kerberos authentication is enabled in Settings > Authentication > Global and the User Directory server type is set to AD, synchronization now uses the Kerberos protocol.
- Added support for converting TCP sessions to PCAP files.
IMPROVEMENTS
- Improved RDP session performance, providing better display quality and increased responsiveness.
- Improved efficiency of converted storage usage to optimize system resource utilization.
- Centralized the OTP generation logic to improve maintainability and consistency across components.
- Added legacy support for VNC environments using the RFB 3.3 protocol.
- Raised the log level for password change information in Fudo to make it more visible in system logs.
- Extended user synchronization attributes to include account expiration date and ensure access control does not rely solely on Active Directory (AD) authentication. This enhancement addresses the fact that AD does not flag expired user accounts as locked, which could result in situations where login remained possible through authentication methods independent of the domain controller. Following this change, Fudo now also synchronizes information regarding account expiration time to prevent users whose AD accounts have expired from logging in, especially in scenarios where the authentication process does not directly involve the domain controller.
Note: Additional safeguards were introduced to prevent the new AD-mapping field from unnecessarily updating the expiration date during sync operations.
API CHANGES
- We've added two new object specifications and group of endpoints, so you can now utilize APIv2 to manage:
- Productivity
- External Storage
DISCONTINUED FEATURES
- The Delta button available for SCP/SFTP sessions in the Session Player view has been removed.
- Fudo Enterprise 5.6 no longer supports the DHCP.
- Fudo Enterprise 5.6 no longer supports the APIv1. All scripts using APIv1 should be rewritten to use APIv2.
- Grant-related endpoints have been removed in the 5.6 release. Please update your integrations accordingly. For more information, refer to the updated API documentation.
- Disabled access to the /api/v2/diagnostics endpoint.
- Fudo Enterprise 5.6 no longer supports the Application to Application Password Manager.
- Fudo Enterprise 5.5 and 5.6 no longer supports the Mobile Token authentication method used to bind the Fudo Officer mobile application to a User. You must unlink all Fudo Officer bindings from Users configuration before the upgrade. For more details, please refer to the 'Before You Upgrade' section below.
ANNOUNCEMENTS
- Fudo Enterprise 5.6 is the last version supporting transparent and gateway modes in the listeners configuration. Listeners using these modes must be reconfigured to use proxy and bastion modes before upgrading to the next release.
- Fudo Enterprise 5.6 is the last version to support bridge interfaces and network interface cards with bypass mode. These components are tightly coupled with the transparent and gateway modes, which will also be removed in version 5.7. We recommend reviewing your network configuration to ensure compatibility with future versions.
- Support for the Telnet 3270 protocol is under review and may be removed in a release following version 5.6. If this protocol is critical to your environment, please contact Fudo Support for more information.
- Support for the 4-Eyes principle, implemented through the Require approval option in safe configuration and used to restrict user access by requiring confirmation, is currently under review and is planned for removal in a future release. Its functionality is largely covered by the Just In Time feature, which we recommend adopting instead. If this functionality is critical to your environment, please contact Fudo Support for more information.
BUG FIXES
- Fixed an issue where upgrading directly from versions 5.5.x to 5.6.2 could result in an inability to authenticate with passwords containing some special characters (version 5.6.2 has since been withdrawn).
- Ensured that all legacy components, references, and artifacts related to the deprecated API version were fully removed after discontinuing its support, leaving the codebase clean and aligned with the current API architecture.
- Fixed an issue in Fudo Officer 2.0 on iOS devices where push notifications for new access requests were delivered without playing the notification sound, despite the app having the required permissions.
- Fixed an issue where access requests were not displayed in Fudo Officer 2.0 when accounts were not linked to a listener.
- Fixed an issue where generating a QR code in Fudo Officer 2.0 failed due to certificate errors, resulting in a 502 response.
- Fixed an issue where an incorrect message about incomplete Fudo Officer 2.0 pairing was displayed even after the device was successfully connected and functioning properly.
- Fixed an issue causing errors during session summary replication in clustered environments.
- Fixed an issue where AI models in clustered environments required retraining after an upgrade.
- Fixed an issue where files downloaded from session playback could differ from the originals transferred during the SFTP session.
- Fixed an issue in retention to ensure session data is only deleted after a successful external backup is confirmed.
- Fixed an issue where revealing a password in the User Access Gateway failed when the account used an SSH key from another account.
- The password changer fails when transport_bind_ip is set to a predefined type and the specified server bind IP is not available on the active password changer node.
- Fixed an issue where the password changer failed when transport_bind_ip was set to a predefined type and the specified bind IP was unavailable on the active node.
- Fixed an issue in the User Directory configuration where changing the Encrypted connection checkbox did not update the Port field, causing incorrect values to persist until the configuration was recreated.
- Fixed an issue where the Common configuration field in RDP functionality safe configuration allowed only a single line of input, instead of supporting multiple lines as in previous versions.
- Fixed an issue where users accessing an active session via a shared link lost real-time screen updates but could still perform operations (join, pause, type, or end the session) if the link was revoked during the session view.
- Fixed an issue that limited the Common configuration field for RDP functionality in safe configuration to a single line instead of allowing multiline input.
- Fixed an issue where the session list appeared empty on the last day of the month due to an incorrect default filter date in the Sessions view.
- Fixed an issue where opening a session fragment containing a searched phrase with special characters caused the Admin Panel to freeze.
- Fixed an issue where multiple redundant OCR processes could start after a Fudo reboot, causing excessive resource usage.
- Fixed an issue where the password changer could fail when `transport_bind_ip` was set to `Any`, affecting configurations modified in recent versions.
- Fixed an issue where users could not log in to UAG when the licensed user limit was exceeded.
- Fixed an issue where sessions restored from backup could not be properly deleted due to permission errors.
- Fixed an issue where connections using native clients through forward accounts with Authenticate against server enabled failed to establish.
- Fixed an issue where assigning or loading more than 1000 objects in the Object Rights and related sections caused data to not load properly.
- Fixed an issue where users without the configuration-read privilege could not access the Backup and Retention page despite having other required permissions.
- Fixed an issue where the Sessions list did not load correctly for users with limited capabilities, causing missing or incorrectly refreshed session pages when navigating or scrolling.
- Closed the possibility to connect to an arbitrary address after successful authentication from within a rendered HTTP session.
- Fixed a missing validation in the network interfaces configuration that allowed saving multiple interfaces with the same subnet.
- Fixed an issue in Network Configuration where renaming an IP label caused a critical database error if the label was used as a bind address in multiple external authentication methods.
- Fixed an issue where LDAP synchronization did not perform incremental updates, functioning only during full synchronization.
- Fixed an issue where the Reset Authentication Failures Counter button did not work for users synchronized from LDAP.
- Fixed an issue where LDAP-synchronized users with access to safes via groups could not send access requests and received a 403 error.
- Fixed an issue where external authentication methods assigned to users synchronized through LDAP or Active Directory were lost after upgrading to a version introducing RBAC changes.
Note: The issue is resolved when upgrading directly from version 5.5 (e.g., 5.5.11/5.5.12) to 5.6.3. However, if an upgrade to 5.6.1 has already caused authentication methods to be lost, updating to 5.6.3 will not restore them. - Fixed an issue where the user list in safe configuration did not display users assigned through Fudo groups.
- Fixed an issue where actions performed by a user who joined a live webclient session were not visible in real time and appeared only after the session ended.
- Fixed an issue where clicking a safe name in the Access via groups section resulted in a 404 error instead of redirecting to the correct safe page.
- Fixed an issue where logging in through external authentication with TLS and no certificate was not possible when Kerberos was disabled.
- Fixed an issue with building the input buffer for pattern matching in terminal protocols (SSH and Telnet).
- Fixed an issue in password changer policies where password complexity options were incorrectly handled after saving, causing unchecked options to become selected.
- Fixed an issue where users could not select External address and port or provide an IP address or FQDN when User Access Gateway was set as the Local address.
- Fixed an issue where downloading the RDP file for a native client connection generated spurious log errors without affecting the connection.
- Fixed an issue where network interface configuration changes made through the UI were not persisted to the database, causing settings to appear saved until a page reload or logout.
- Fixed an issue where the Retention module attempted to remove session replicas stored on external backup servers, resulting in warning logs and skipped sessions.
- Fixed an issue where certain fields were missing from email notifications, including management URL and user details for session join and leave events.
- Fixed an issue where users were no longer notified about already active sessions after upgrading to version 5.6.1.
- Fixed an issue where only one network interface was displayed in redundancy group configuration instead of all properly addressed interfaces.
- Fixed an issue where TDS sessions were not indexed.
- Fixed an issue where fetching the destination server certificate failed when using a labeled IP address.
- Fixed an issue in the RDS implementation where external connections through UAG were not properly recognized, causing dropped connections after redirection from the RDS broker.
- Fixed an issue where saving group option changes took an unusually long time and checkbox selections behaved inconsistently.
- Fixed an issue where the Object Rights table displayed Role name instead of User name in the Assign user view.
- Fixed an issue where the list of authentication methods for local users displayed only hostnames or IP addresses instead of method names, making it difficult to identify the correct method.
- Fixed an issue where the Search function did not filter Policies or Regular Expressions, preventing users from sorting results.
- Fixed an issue in the Productivity tab where the 6-month and 1-year filters in session comparison displayed data for incorrect date ranges.
- Fixed an issue where object lists in GUI filters were not sorted, causing the newest objects to appear at the top instead of in a consistent order.
- Improved the warning message displayed when modifying a time policy assigned to multiple users or groups to provide clearer guidance.
- Improved the display of revealed passwords in the User Access Gateway to properly handle multiline secrets by showing them in a text area instead of a single line.
- Fixed layout issues in the Password history view in User Access Gateway, where the Back button was misaligned for accounts with long passwords or SSH keys. Also improved the display of multiline secrets.
- Corrected Russian and Ukrainian UI translations to fix a few mismapped labels and ensure clarity and consistency.
- Fixed an issue where files transferred via Fudo using SCP were saved with randomized names and missing file extensions.
- Fixed an issue in UAG where native client connections to accounts assigned to a server pool ignored the selected server and connected to the first host or mask in the list.
- Fixed an issue where connections handled exclusively through Fudo Share Access incorrectly consumed Fudo Enterprise licenses or restricted access despite the limited license not applying to Fudo Share Access.
- Fixed an issue where unpairing Fudo Enterprise from Fudo Share Access (FSA) removed the FSA key field, preventing re-pairing with another environment.
- Fixed an issue where Fudo Share Access failed to generate OTPs for imported Active Directory groups.
- Fixed an issue where cluster pairing failed due to a missing private EC key.
- Fixed an issue in Fudo Share Access where notification emails were missing for share confirmation and access request approval or rejection.
BEFORE YOU UPGRADE
It is highly recommended to perform the 'Upgrade check' before the proper upgrade. The result of the failed check may contain information about configuration changes that needs to be done by a Fudo administrator to successfully upgrade Fudo.
There are a few things that need to be verified before this upgrade can be applied:
- Make sure your Fudo instance isn’t undergoing any system-wide process, such as storage rebuild, or the system isn’t under full-load.
- In a cluster configuration, make sure all nodes are synchronized and upgrade the slave node first.
- Make sure you have an active Premium or Standard Support maintenance contract.
Licensing Changes
Starting with version 5.6, license enforcement logic has been updated as part of the RBAC introduction:
- In version 5.5, superadmin users were always counted as active and had priority in login rights.
- In version 5.6, logins of users with administrative privileges to the Admin Panel are always prioritized, regardless of the current license limits. Their logins are now counted as standard authentications within the licensing scope.
|
Note: When the number of active users reaches the license limit and a new user logs into the Admin Panel, the system now prioritizes users with management access. In this case, the user who logged into User Access Gateway (UAG) earliest will lose access, as the privileged user is now counted as active. Existing sessions of the user who lost access are not terminated — they continue to run as usual. |
TDS Kerberos Delegation
For Kerberos authentication to work correctly, the server configuration must use the Host option in the Destination section. Configurations using an IP address will fail because Kerberos relies on hostname-based SPN (Service Principal Name) resolution.
DHCP Discontinuity
Starting from version 5.6.1, DHCP is no longer supported. If DHCP is enabled in the existing configuration, the upgrade process will be blocked. To proceed with the upgrade, ensure that all DHCP-related settings are removed or replaced with static network configuration before initiating the upgrade.
External Authentication - Active Directory
In previous releases, when configuring external authentication through Active Directory with TLS enabled, it was possible to upload a server certificate. Starting from this release, Fudo only supports a CA certificate. If a server certificate is currently configured, you must change its value to None before upgrading.
Handling Legacy Checkout Sessions
During the upgrade to version 5.6.1, environments containing checkout sessions that still reference the deprecated SAFE_SYSTEM_ID are automatically handled as follows:
- Deleted checkout sessions referencing SAFE_SYSTEM_ID are removed.
- A new safe is created with the ID MIGRATED_CHECKOUT_SAFE_ID (value: 200) and the name 'Migrated checkout sessions'.
- Remaining (non-deleted) checkout sessions are reassigned from SAFE_SYSTEM_ID to MIGRATED_CHECKOUT_SAFE_ID.
These changes ensure that the upgrade process completes successfully in environments previously migrated to Fudo 4.3.
|
Note: The safe 'Migrated checkout sessions' is created only if the sessions described above exist in the system. |
Mobile Token
|
Note: Fudo Enterprise 5.6 and later versions no longer support the Mobile token authentication method used to bind Fudo Officer mobile application to a User. Please ensure that the mobile application is unlinked from any User configuration. Otherwise, the upgrade will fail, and the script UPG000685 will return a list of users who have the mobile application linked. |
To unlink the Fudo Officer mobile application, please edit the user configuration, then:
- Go to the 'More' tab, and in the 'Fudo Officer' section, unlink the application using the 'Cancel binding' button.
- Alternatively, go to the 'Settings' tab, in the 'Authentication' section find the 'Mobile token' method and remove it using the 'Delete' button.
Transition to RBAC After Upgrade
|
Note: In the RBAC model, the *-read privilege grants visibility into a specific tab of the interface, and consequently, into all objects of that type in the system—not just those for which the user has capabilities. This privilege provides view-only access and does not permit editing, deletion, or any other actions. |
- Listener Access Model Updated: With the introduction of RBAC, users now either have access to all listeners or to none. Granting access to individual listeners is no longer possible.
- Access Request Voting: Now requires both `access-request-read` and `access-request-vote` privileges, as well as `read` access to the associated user, safe, and account.
- Superadmin, Admin, and Operator Roles After Upgrade: These roles are preserved during the transition to RBAC, with their permissions mapped to ensure comparable access as before. Note that some exceptions apply, and the mapping may not reflect a one-to-one correspondence in all cases. Selected examples include:
- After the upgrade, an admin who has a capability assigned to an object will automatically gain full permissions for that object.
- Since listeners are considered a global and network-level configuration, after upgrading to version 5.6, admin users no longer have permissions to create them.
- The Authentication tab is now available to users with the admin, safe admin and operator roles by default (`extauth-read` privilege) to be able to see or assign external authentication to other users.
- The admin, safe admin and operator roles now have access to the External Password Repositories tab (`passvn-read` privilege) to be able to see or assign external password repositories to accounts.
- The admin, safe admin and operator roles now have access to the Cluster tab (`cluster-read` privilege) by default, allowing them to send sessions to other nodes.
- The operator role now includes the `listener-read` privilege by default. However, due to RBAC changes, operators can currently view all listeners, not just those explicitly granted.
- A user with the session viewer role can now access the Download > Files tab and download files listed there. This permission is required for the correct display of SFTP/SCP sessions.
- The session viewer role now includes access to additional interface elements, such as new tabs (e.g., Users, Servers, Accounts, Safes) and the ability to add the Active Users dashlet from the Dashlet Marketplace, depending on the assigned capabilities.
- Operators, session viewers, safe admin, and other custom roles will now be able to see all existing anonymous sessions as well as any new sessions initiated by anonymous users.
- The predefined user and service roles have been removed.
- After upgrading to version 5.6, any users who previously had this role assigned will no longer have any role.
- Before the upgrade, customers who previously had multiple users assigned to the service role must remove all but one of them.
- SNMP settings previously configured for that user will be transferred to the System tab and applied globally.
|
Note: The predefined roles serve as a transitional starting point and are fully editable (with the exception of superadmin). The automatic mapping of legacy roles is a one-time compatibility step performed only during the upgrade from a version without RBAC. These predefined roles are not intended to replicate previous permissions one-to-one, but rather to provide a starting point for adaptation. We recommend reviewing all assigned privileges after the upgrade to ensure they reflect your security requirements. |
MySQL Listeners
TLS is now required for MySQL listeners. In previous versions, TLS could not be enabled for MySQL listeners or servers. As a result, any existing MySQL listeners will become non-functional after the upgrade. To restore connectivity, administrators must manually enable TLS and configure a valid certificate for the listener.
Kerberos Support for User Directory Synchronization
If you plan to use Kerberos authentication for User Directory synchronization, ensure the following before upgrading:
- Port 88 (Kerberos) is open on the firewall — otherwise, synchronization will fail.
- The Fudo hostname includes the appropriate domain suffix (for example, fudo.qa.kerberos).
- The DNS server from the same domain is properly configured.
- The controller address matches the SPN (Service Principal Name) of the LDAP server defined in the domain.
If your current configuration uses an IP address instead of a hostname, update it to use the correct hostname before upgrading.
|
Note: If you do not intend to use Kerberos, disable it in the Settings > Authentication > Global tab to continue using simple bind for synchronization. |
RECOMMENDED UPGRADE PATH
Before proceeding with the upgrade, please verify the version number of your Fudo Enterprise instance. Depending on the version number, you will need to follow a specific upgrade path. To learn more, please refer to the Fudo Enterprise Product Upgrade Path article.
|
Note: Fudo Enterprise 5.4.12 introduces a new upgrade barrier in the Product Upgrade Path. If you are upgrading from any version of Fudo 5.4, please ensure you upgrade to at least version 5.4.12 before proceeding to version 5.6.x. |
HOW TO UPGRADE YOUR FUDO
- Login to your Fudo Admin Panel.
- Select 'Settings > System' from the main menu on the left-hand side and go to the 'Upgrade' tab.
|
Note: If your Fudo is running in a cluster, start the upgrade on the Slave node, and only when the upgrade finishes successfully start upgrading the Master node. When both systems are running the same Fudo version cluster communication will be restored. |
- Select 'Upload' from the top right side and upload the previously downloaded and unzipped upgrade package file.
- Select 'Run Check' to determine if your upgrade file is correct and can be applied to the existing Fudo configuration. Refresh your browser window to see 'Upgrade check' current progress.
- Upon a successful 'Run Check' result, upgrade your Fudo by using the 'Upgrade' button. Upon system restart, all active sessions will be terminated.
|
Note: In case of an unsuccessful check do not upgrade your system, double check your upgrade file checksum. If you encounter any problems, get in touch with us and we will assist you. |
HOW TO IMPORT SYSTEM CONFIGURATION
|
Note:
|
- Login to your Fudo Admin Panel.
- Select Settings > System from the main menu on the left-hand side.
- Go to the Configuration tab.
- Upload the 'Master key' file and 'Configuration file' exported from another Fudo instance and click Import to proceed with initiating the system with the imported data.
|
Note: For more details, please refer to the 'Exporting/Importing System Configuration' section of the Fudo Enterprise documentation. |
THE ROLLBACK PROCEDURE
If you are experiencing issues with the newly installed version, you have an option to roll back to the previous version of Fudo running on this machine. To do so, click the user menu on the top right, select 'Reboot', and select previous system revision from the drop-down list.
|
Note: Please note that if upgrading from version 5.5 or earlier, both session recordings and any changes to RBAC roles or groups made in the newer version will be lost after rollback. |
DOWNLOAD
Download Fudo Enterprise 5.6.3
Download PDF version of this Release Note.
CONTACT US
If you have questions or concerns, please get in touch at support@fudosecurity.com or by phone: +48 22 100 67 09.
Sincerely,
Fudo Security Team
Fudo Enterprise 5.6.2
Date: October 2025
Dear Partners,
We would like to inform you that due to certain issues identified after upgrading to version 5.6.2, we have decided to temporarily withdraw this release from distribution. This decision was made to ensure the highest stability and quality of our solutions.
Our technical team is actively working on identifying the root cause and preparing a corrected version, which will be made available as soon as possible.
We appreciate your understanding and apologize for any inconvenience this may cause.
Best regards,
Fudo Security Team
Fudo Enterprise 5.6.1
Date: August 2025
This is a major Fudo release, introducing a range of improvements and new fixes.
HOTFIX REQUIRED FOR THIS VERSION
Please install the following hotfixes along with this version of Fudo Enterprise — download them from SOFTWARE & DOCUMENTATION > Software Hotfix
- Hotfix for Rendered HTTP Session Issue in 5.6.0 and 5.6.1
- Hotfix for Rendered HTTP Session Issue in 5.6.0 and 5.6.1
- Hotfix for Just-in-Time Access Request and Translation Issues in 5.6.1
NEW FEATURES
ROLE-BASED ACCESS CONTROL
In this Fudo Enterprise version we gladly introduce RBAC (Role-Based Access Control) - feature, which brings significant improvements in access management.
List of improvements within RBAC:
- Creating custom roles – Administrators can create roles with precisely defined permissions tailored to specific tasks, instead of relying solely on the predefined roles as before.
- Managing selected object types – Roles can be narrowed down to manage only selected types of objects, such as Users, Listeners, Pools, Servers, or Safes.
- Assigning action scope on objects – Permissions can be limited to specific actions, such as creating, modifying, exporting, deleting, or blocking particular types of objects.
- Flexibility in assigning permissions – Permissions can be granted globally or selectively, e.g., to all objects of a certain type (e.g., Users, Accounts, or Servers) or only to selected, specific objects.
- Access management by specific tabs – The ability to create roles with access limited to selected tabs within Fudo Enterprise.
- Multi-role assignment – Users will be able to receive multiple roles, rather than just one of the six predefined roles as was the case before.
GROUPS
We’re introducing a new object—Group—that adds an extra layer of control over resource access. Administrators can now create user groups to grant more precise permissions, ensuring that only authorized users can interact with specific Safes. Additionally, it is now possible to view which Safes a user has access to through the groups they belong to.
AI SESSION SUMMARY
Fudo Enterprise 5.6 introduces a beta version of AI-powered summaries for SSH sessions. This feature allows administrators to quickly assess session context without replaying full recordings, improving audit efficiency and reducing manual review time. The feature can be easily configured with AI providers such as OpenAI, Anthropic, or a custom model using a local Ollama framework.
GRANULAR ACCESS TO REMOTE APPLICATIONS
To improve access control and reduce surface exposure, this version adds support for restricting users to specific remote applications without granting access to the full desktop environment. This enhancement enables more granular permission management and helps ensure that users interact only with the resources necessary for their roles.
TUNNEL LISTENERS
Fudo Enterprise 5.6 introduces a new Listener type that allows establishing an SSH tunnel for more secure connections. With this feature, administrators can safely enable access to protocols that are not encrypted by default, such as Telnet or VNC, while also adding an optional layer of encryption to other supported protocols.
ADDITIONAL NEW FEATURES AND IMPROVEMENTS
- Port Ranges: Added support for configuring Server objects with a port range, simplifying multi-port redirection and reducing manual setup.
- Added support for configuring an outbound HTTP proxy for authentication-related traffic (OIDC, SMS, DUO). Also usable for timestamping services. Support for more integrations coming in future releases.
- Added the ability to specify a remote application when establishing a session through the web client.
- Enhanced MySQL protocol support:
-
- Added support for Bastion connections
- Enabled authentication against the MySQL server
- Supported all authentication methods, including one-step multi-factor (e.g., password+token)
- Supported authentication plugins:
- for communication between Fudo and the database server: mysql_clear_password, mysql_native_password, caching_sha2_password;
- for communication between the client and Fudo: mysql_clear_password.
- Reorganized Interface Elements:
- Export/Import Configuration options have been relocated from the user menu (top-right corner) to System > Configuration for improved visibility and accessibility.
- The Timestamping settings have been moved from a standalone tab to Settings > System, aligning with other system-level configuration options.
- The former LDAP Synchronization tab has been replaced with User Directory, reflecting its broader functionality and redesigned layout.
- A new Object Rights subtab has been added to the editing views of Servers, Accounts, Pools, and Safes. This change, introduced with role-based access control (RBAC), enables administrators to define which users or roles are authorized to manage a given object—supporting more granular delegation of access rights.
- User mapping in the User Directory has been redesigned — users are now assigned to groups instead of safes. This simplifies configuration and enables more flexible, centralized control over user permissions.
- Nearly all configuration tabs in Fudo Enterprise have now been fully migrated to the new graphical interface. Each redesigned tab features improved clarity, faster navigation, and consistent behavior. Overview of Updated Tabs:
- Sessions tab – Redesigned layout with labeled action buttons and a customizable column view. Less-used fields moved under a three-dot menu.
- System tab – New Configuration subtab for export/import. Diagnostics split into focused subtabs for better clarity.
- Network Configuration tab – Refreshed visuals and clearer layout for managing interfaces and routes.
- Reports tab – Unified table view for all report types and schedules. Simplifies configuration and overview.
- Cluster tab – Split into Create cluster and Join cluster tabs for more intuitive setup.
- Notifications tab – Updated layout aligned with the new interface style. Improved readability.
- User Directory tab – Formerly LDAP Synchronization. Restructured with modal windows for cleaner configuration.
- External Storage tab – Updated to match the modernized UI. Minor usability enhancements.
- Productivity tab – Updated to match the modernized UI. Minor usability enhancements.
- The Session Player interface has been refreshed to enhance usability. Key control buttons have been repositioned for improved visibility and a more intuitive playback experience.
- Enhanced Listener configuration for User Access Gateway. Administrators can now bind Listeners directly to the UAG address, simplifying native client connections and improving flexibility when UAG operates on multiple addresses.
Note: Customers who want to listen on both an external address and local addresses should create two separate listeners: one for the external address and one for local addresses. - Added support for mapping OIDC configurations to Fudo domains. This allows assigning an OIDC configuration to a specific domain, resolving conflicts where users with identical user IDs originate from different LDAP/AD synchronizations.
- Added support for custom TLS certificates in OIDC configuration. Administrators can now specify the CA certificate that signed the OIDC server certificate, provide a custom server certificate, or continue using the system root CA repository as before.
- Added support for clustered environments in ShareAccess. When Fudo Enterprise instances are configured in a high-availability cluster, they can now be connected to ShareAccess as gateway nodes, ensuring redundancy and seamless failover.
API CHANGES
- The transition to APIv2 continues, bringing numerous new endpoints designed to enhance functionality and streamline the process of rewriting tabs to the new API. Consequently, this update aims to significantly improve performance and expand overall capabilities.
- We've added numerous new object specifications and endpoints to our Fudo Enterprise 5.6 APIv2, so you can now utilize it to manage:
- Roles (RBAC)
- Groups (RBAC)
- Capabilities for objects (RBAC)
- Sessions, including:
- Timestamping
- OCR
- Approve/Reject actions
- Comments
- Last activity tracking
- Replication
- Restoring
- Sharing and revoking shared sessions
- Terminating
- Downloading
- User Directory (formerly LDAP Synchronization)
- Password changers and remote applications in accounts
- Discovery scanners and rules
- Upgrade process
- License management
- Hotfix installation
- Defined reports
- Remote applications (new endpoints)
- Configuration import/export
- IPMI port configuration
DISCONTINUED FEATURES
- Fudo Enterprise 5.6 no longer supports the DHCP.
- Fudo Enterprise 5.6 no longer supports the APIv1. All scripts using APIv1 should be rewritten to use APIv2.
- Grant-related endpoints have been removed in this release. Please update your integrations accordingly. For more information, refer to the updated API documentation.
- Disabled access to the /api/v2/diagnostics endpoint.
- Fudo Enterprise 5.6 no longer supports the Application to Application Password Manager.
- Fudo Enterprise 5.5 and 5.6 no longer supports the Mobile Token authentication method used to bind the Fudo Officer mobile application to a User. You must unlink all Fudo Officer bindings from Users configuration before the upgrade. For more details, please refer to the 'Before You Upgrade' section below.
ANNOUNCEMENTS
- Fudo Enterprise 5.6 is the last version supporting transparent and gateway modes in the listeners configuration. Listeners using these modes must be reconfigured to use proxy and bastion modes before upgrading to the next release.
- Fudo Enterprise 5.6 is the last version to support bridge interfaces and network interface cards with bypass mode. These components are tightly coupled with the transparent and gateway modes, which will also be removed in version 5.7. We recommend reviewing your network configuration to ensure compatibility with future versions.
- Support for the Telnet 3270 protocol is under review and may be removed in a release following version 5.6. If this protocol is critical to your environment, please contact Fudo Support for more information.
- Support for the 4-Eyes principle, implemented through the Require approval option in safe configuration and used to restrict user access by requiring confirmation, is currently under review and is planned for removal in a future release. Its functionality is largely covered by the Just In Time feature, which we recommend adopting instead. If this functionality is critical to your environment, please contact Fudo Support for more information.
BUG FIXES
- Fixed an issue where changing the organization owner in ShareAccess could fail due to insufficient permissions.
- Fixed an issue where RDP authentication failed when using a native client and the system keyboard input language was set to Russian, for users with OATH enabled.
- Fixed a limitation preventing bulk account removal from safes with multiple listeners.
- Fixed an issue that could cause cluster freeze due to incorrect locking.
- Fixed an issue where a single failed Kerberos login caused multiple failed attempts in Active Directory, leading to account lockout, by adding handling for specific failure reasons such as incorrect password, locked account, or expired password.
- Implemented caching to avoid repeated attempts to contact unreachable KDC servers.
- Implemented infinite scroll in areas handling large datasets, including password changers, password verifiers, and remote applications, to ensure consistent and reliable data loading across the interface.
- Fixed a conversion error that occurred when downloading restored sessions in formats other than TGZ or text log.
- Fixed an issue where the HTTPS listener returned only the server certificate, omitting the intermediate certificate from the configured chain during SSL handshake.
- Fixed an issue where transport certificates added manually to password changer configuration were saved in an incorrect format, causing certificate parsing failures and preventing proper operation.
- Fixed an issue where timeout settings were not correctly applied, causing early logouts for User Access Gateway users and no timeout enforcement for users on the Admin Panel interface.
- Fixed incorrect visual indicators for disk statuses on the dashboard, ensuring consistent representation for "Synchronizing" and "Warning" states.
- Fixed an issue preventing users from logging out due to a missing X-CSRFToken header.
- Fixed an issue where incorrectly generated empty email files caused an internal server error in the Notification tab.
- Fixed an issue where SFTP backups to servers using RebexSSH failed with a "Badly formed packet received" error, preventing session data transfer.
- Fixed an issue where manually replicated sessions with 'database' replication only failed to play, displaying a black screen despite showing playback progress.
- Fixed an issue where removing an external AD authentication server did not delete its associated certificate, causing upgrade failures due to leftover configuration artifacts.
- Fixed an issue causing XML response parsing failures when retrieving passwords from the Delinea (Thycotic) External Password Repository, which resulted in authentication errors.
- Corrected the Russian translation of the Armenian language name in the OCR language selection list.
- Fixed an issue related to SNMP communication being resynchronized, where Zabbix connections failed after some time.
- Fixed an issue where users could not authenticate with CERB as the first factor when using the External Authentication + Duo method, preventing successful login.
- Fixed incorrect behavior of partial synchronization in environments with multiple synchronization sources and mappings, where users could be incorrectly removed from safes shortly after being added, despite valid assignments.
- Fixed an issue where users were not removed from Fudo groups after being removed from the corresponding AD groups during synchronization.
- Fixed an issue where the AD group search in User Directories did not support SSL certificate chains, preventing successful LDAP connections when multiple certificates were provided.
- Fixed an issue preventing OTP generation for forward-type accounts when users logged into the User Access Gateway via OpenID without a configured secret in MGMT.
- Fixed an issue where uploading an HTTPS certificate with an encrypted private key to the User Access Gateway or Admin Panel failed silently, with no error or warning shown in the UI or API response.
- Fixed an issue where connections failed if a server and an account shared the same name, causing the system to locate the server but not the corresponding account.
- Fixed an issue where the 'Join' button was missing when accessing a shared session link without the 'Read only' option enabled, preventing anonymous users from joining active sessions as intended.
- Fixed an issue where ldapsyncd failed to remove users from Fudo after they were deleted from the mapped Active Directory group due to insufficient SQL grants.
- Removed outdated JavaScript libraries to address potential security and compatibility issues.
- Fixed an issue where configuring SMTP with certain authentication types (Login, NTLM, Digest MD5, or External) caused notifications to fail and test connections to return errors.
KNOWN ISSUES
- AI models trained on a specific version must be retrained after an upgrade in clustered environments. The issue does not occur when upgrading a single-node (master) deployment.
- Multiple redundant OCR processes may start after a Fudo reboot, leading to unnecessary resource usage.
- LDAP Synchronization may not perform incremental updates, while full synchronization works correctly.
BEFORE YOU UPGRADE
It is highly recommended to perform the 'Upgrade check' before the proper upgrade. The result of the failed check may contain information about configuration changes that needs to be done by a Fudo administrator to successfully upgrade Fudo.
There are a few things that need to be verified before this upgrade can be applied:
- Make sure your Fudo instance isn’t undergoing any system-wide process, such as storage rebuild, or the system isn’t under full-load.
- In a cluster configuration, make sure all nodes are synchronized and upgrade the slave node first.
- Make sure you have an active Premium or Standard Support maintenance contract.
TDS Kerberos Delegation
For Kerberos authentication to work correctly, the server configuration must use the Host option in the Destination section. Configurations using an IP address will fail because Kerberos relies on hostname-based SPN (Service Principal Name) resolution.
DHCP Discontinuity
Starting with this version, DHCP support has been removed. To ensure a successful upgrade, review your configuration in advance and replace all DHCP-related settings with static network configuration.
External Authentication - Active Directory
In previous releases, when configuring external authentication through Active Directory with TLS enabled, it was possible to upload a server certificate. Starting from this release, Fudo only supports a CA certificate. If a server certificate is currently configured, you must change its value to None before upgrading.
Handling Legacy Checkout Sessions
During the upgrade to version 5.6.1, environments containing checkout sessions that still reference the deprecated SAFE_SYSTEM_ID are automatically handled as follows:
- Deleted checkout sessions referencing SAFE_SYSTEM_ID are removed.
- A new safe is created with the ID MIGRATED_CHECKOUT_SAFE_ID (value: 200) and the name 'Migrated checkout sessions'.
- Remaining (non-deleted) checkout sessions are reassigned from SAFE_SYSTEM_ID to MIGRATED_CHECKOUT_SAFE_ID.
These changes ensure that the upgrade process completes successfully in environments previously migrated to Fudo 4.3.
|
Note: The safe 'Migrated checkout sessions' is created only if the sessions described above exist in the system. |
AI Models Retraining in Clustered Environments
When upgrading a clustered deployment, AI models trained on a previous version must be retrained after the upgrade. This limitation does not apply to single-node deployments, where existing models continue to work correctly without retraining.
Mobile Token
|
Note: Fudo Enterprise 5.6 and later versions no longer support the Mobile token authentication method used to bind Fudo Officer mobile application to a User. Please ensure that the mobile application is unlinked from any User configuration. Otherwise, the upgrade will fail, and the script UPG000685 will return a list of users who have the mobile application linked. |
To unlink the Fudo Officer mobile application, please edit the user configuration, then:
- Go to the 'More' tab, and in the 'Fudo Officer' section, unlink the application using the 'Cancel binding' button.
- Alternatively, go to the 'Settings' tab, in the 'Authentication' section find the 'Mobile token' method and remove it using the 'Delete' button.
Transition to RBAC After Upgrade
|
Note: In the RBAC model, the *-read privilege grants visibility into a specific tab of the interface, and consequently, into all objects of that type in the system—not just those for which the user has capabilities. This privilege provides view-only access and does not permit editing, deletion, or any other actions. |
- Listener Access Model Updated: With the introduction of RBAC, users now either have access to all listeners or to none. Granting access to individual listeners is no longer possible.
- Access Request Voting: Now requires both `access-request-read` and `access-request-vote` privileges, as well as `read` access to the associated user, safe, and account.
- Superadmin, Admin, and Operator Roles After Upgrade: These roles are preserved during the transition to RBAC, with their permissions mapped to ensure comparable access as before. Note that some exceptions apply, and the mapping may not reflect a one-to-one correspondence in all cases. Selected examples include:
- After the upgrade, an admin who has a capability assigned to an object will automatically gain full permissions for that object.
- Since listeners are considered a global and network-level configuration, after upgrading to version 5.6, admin users no longer have permissions to create them.
- The Authentication tab is now available to users with the admin, safe admin and operator roles by default (`extauth-read` privilege) to be able to see or assign external authentication to other users.
- The admin, safe admin and operator roles now have access to the External Password Repositories tab (`passvn-read` privilege) to be able to see or assign external password repositories to accounts.
- The admin, safe admin and operator roles now have access to the Cluster tab (`cluster-read` privilege) by default, allowing them to send sessions to other nodes.
- The operator role now includes the `listener-read` privilege by default. However, due to RBAC changes, operators can currently view all listeners, not just those explicitly granted.
- A user with the session viewer role can now access the Download > Files tab and download files listed there. This permission is required for the correct display of SFTP/SCP sessions.
- The session viewer role now includes access to additional interface elements, such as new tabs (e.g., Users, Servers, Accounts, Safes) and the ability to add the Active Users dashlet from the Dashlet Marketplace, depending on the assigned capabilities.
- The predefined user and service roles have been removed.
- After upgrading to version 5.6, any users who previously had this role assigned will no longer have any role.
- Before the upgrade, customers who previously had multiple users assigned to the service role must remove all but one of them.
- SNMP settings previously configured for that user will be transferred to the System tab and applied globally.
|
Note: The predefined roles serve as a transitional starting point and are fully editable (with the exception of superadmin). The automatic mapping of legacy roles is a one-time compatibility step performed only during the upgrade from a version without RBAC. These predefined roles are not intended to replicate previous permissions one-to-one, but rather to provide a starting point for adaptation. We recommend reviewing all assigned privileges after the upgrade to ensure they reflect your security requirements. |
MySQL Listeners
TLS is now required for MySQL listeners. In previous versions, TLS could not be enabled for MySQL listeners or servers. As a result, any existing MySQL listeners will become non-functional after the upgrade. To restore connectivity, administrators must manually enable TLS and configure a valid certificate for the listener.
RECOMMENDED UPGRADE PATH
Before proceeding with the upgrade, please verify the version number of your Fudo Enterprise instance. Depending on the version number, you will need to follow a specific upgrade path. To learn more, please refer to the Fudo Enterprise Product Upgrade Path article.
|
Note: Fudo Enterprise 5.4.12 introduces a new upgrade barrier in the Product Upgrade Path. If you are upgrading from any version of Fudo 5.4, please ensure you upgrade to at least version 5.4.12 before proceeding to version 5.6.x. |
HOW TO UPGRADE YOUR FUDO
- Login to your Fudo Admin Panel.
- Select 'Settings > System' from the main menu on the left-hand side and go to the 'Upgrade' tab.
|
Note: If your Fudo is running in a cluster, start the upgrade on the Slave node, and only when the upgrade finishes successfully start upgrading the Master node. When both systems are running the same Fudo version cluster communication will be restored. |
- Select 'Upload' from the top right side and upload the previously downloaded and unzipped upgrade package file.
- Select 'Run Check' to determine if your upgrade file is correct and can be applied to the existing Fudo configuration. Refresh your browser window to see 'Upgrade check' current progress.
- Upon a successful 'Run Check' result, upgrade your Fudo by using the 'Upgrade' button. Upon system restart, all active sessions will be terminated.
|
Note: In case of an unsuccessful check do not upgrade your system, double check your upgrade file checksum. If you encounter any problems, get in touch with us and we will assist you. |
HOW TO IMPORT SYSTEM CONFIGURATION
|
Note:
|
- Login to your Fudo Admin Panel.
- Select Settings > System from the main menu on the left-hand side.
- Go to the Configuration tab.
- Upload the 'Master key' file and 'Configuration file' exported from another Fudo instance and click Import to proceed with initiating the system with the imported data.
|
Note: For more details, please refer to the 'Exporting/Importing System Configuration' section of the Fudo Enterprise documentation. |
THE ROLLBACK PROCEDURE
If you are experiencing issues with the newly installed version, you have an option to roll back to the previous version of Fudo running on this machine. To do so, click the user menu on the top right, select 'Reboot', and select previous system revision from the drop-down list.
|
Note: Please note that if upgrading from version 5.5 or earlier, both session recordings and any changes to RBAC roles or groups made in the newer version will be lost after rollback. |
DOWNLOAD
Download Fudo Enterprise 5.6.1
Download PDF version of this Release Note.
CONTACT US
If you have questions or concerns, please get in touch at support@fudosecurity.com or by phone: +48 22 100 67 09.
Sincerely,
Fudo Security Team